Architecture Overview
Originally created at the Walt Disney Company in 2014, Dragonchain is a hybrid blockchain platform focused on solving business problems at an enterprise scale. The Dragonchain Architecture Document was created and published in 2016, in advance of the open source release of the software created at Disney. The the Dragonchain Architecture Document. has remained largely unchanged since its release. The document describes the philosophy, reasoning, and structure behind the hybrid blockchain verification process.
Key elements within the document include an itemization architectural goals and a new concept for blockchain consensus termed Context Based Verification.
Architectural Goals
Dragonchain’s architectural (and project) goals were very unique at the time, focusing on scalability and interoperability with a business and enterprise focus. They have stood the test of time and remain our goals.
Ease of integration of existing systems
Ease of development for traditional engineers and coders unfamiliar with blockchain, distributed systems, and cryptography
Client server style and simple RESTful integration points for business integration
Simple architecture (exible and usable for unforeseen applications)
Provide protection of business data by default
Allow business focused control of processes
Fixed length period blocks
Short/fast blocks
Currency agnostic blockchain (multi-currency support)
No base currency
Interoperability with other blockchains public and private
Adoption of standards as they become available
Consensus: Context Based Verification
Context Based Verification provides a business chain with verifications from distributed nodes within the Dragonchain verification network (Dragon Net) based on multiple business contexts at multiple “levels”. The reference implementation defines five levels of verification:
Level 1 - Business (Approval) Verfication – Business approval of transaction and payload
Level 2 - Enterprise (Validation) Verification – Network (non-payload) validation of transaction
Level 3 - Network Diversity Verification – Validator node (L2) diversity check
Level 4 - External Partner (Notary) Verification – Independent proof of existence verification (owner identity verified). Originally, in the enterprise, this was intended to be run by outside business partners. On the current Dragonchain platform, Notary chains (L4) are only run by identified organizations and users.
Level 5 - Public Checkpoint – a hash of multiple L4 blocks are sent to various external or foreign blockchains (e.g. Bitcoin, Ethereum, and Ethereum Classic) to leverage the foreign chain’s hashpower or network to secure transactions.
Level X - Proprietary Context Verification – Any desired business context may be included in the standard verification of business data on a Dragonchain business chain (L1).
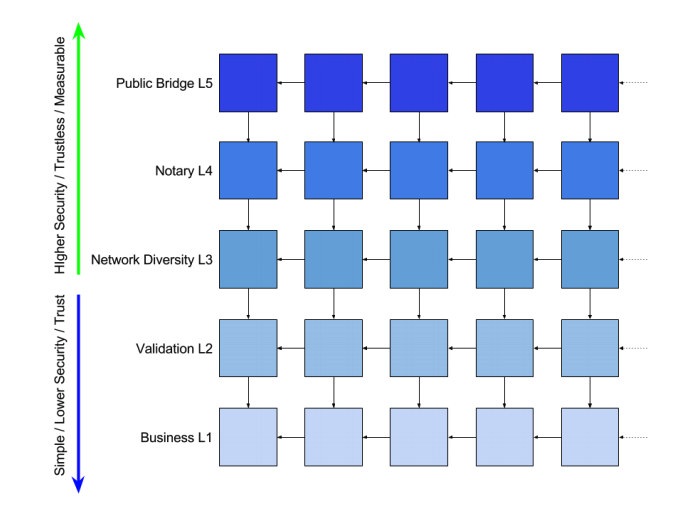
The "blockchain of blockchains" architecture described above
Unlike many other blockchain solutions, Dragonchain is a hybrid blockchain platform. Through Dragon Net, every transaction on your business chain is secured with the combined power of multiple public blockchain networks (e.g. Bitcoin & Ethereum). To do this, the Dragonchain Architecture separates the concept of proof from payload, decentralizing the proof alone. Potentially sensitive business data (and business logic) is by default not exposed to the verification network, or any outside blockchain. This means that the verification network need not understand anything about your data types, standards, or proprietary classifications.
Dragonchain organizes its network into five separate levels. A business chain (L1), is a totally private blockchain only accessible through use of access credentials. All transaction data is ledgered and all smart contract business logic is executed directly on this chain.
The business chain creates a new block every 5 seconds, if and only if new transactions are present. After creating a block, the business chain broadcasts a sanitized version stripped of sensitive private data to Dragon Net. This block will then progress through all 5 levels of verification context. This decentralization of proof ensures that the business block and its transactions have not been compromised or tampered with. Finally, the hash of these many business chain blocks are ledgered onto several public blockchains (e.g. Ethereum, Bitcoin, Ethereum Classic, etc.) to leverage their massive combined hash power and network effect, and to provide measurable proof for all business chain transactions.
Dragon Net can be thought of as a “blockchain of blockchains”, where every level is a complete private blockchain. Because the business chain obtains verification from multiple other chains, transaction proof is distributed across the network for efficient and fast decentralization.
To learn more about Dragonchain architecture, see the Dragonchain Architecture Document.
To learn more about the reference implementation of the Dragonchain Architecture, see the Dragonchain core documentation architecture section.